What are DNS blocks?
DNS blocks stop a hostname from resolving. A resolver can answer NXDOMAIN or NODATA, return a sinkhole IP like 0.0.0.0 or a block page, or reply REFUSED. The connection that depends on the name never starts.
- Why: reduce risk and enforce policy across all devices using the resolver.
- Scope: works without endpoint agents; applies to names, not direct IPs.
- Limits: can be bypassed; doesn't inspect content or decrypt HTTPS.
Who uses DNS blocking?
DNS blocking is used by different groups for different objectives. The mechanism is the same, the policy differs.
Businesses and schools
- Reduce risk by blocking domains linked to malware, phishing, and command‑and‑control.
- Limit distraction or legal exposure by applying categories such as gambling or adult content.
- Apply consistent safeguards to all devices using the network, including BYOD.
Families and individuals
- Use family presets to filter adult content or obvious scam domains.
- Prefer resolvers that publish clear privacy policies and allow easy overrides.
ISPs and governments
- Comply with court orders or codes of practice by applying resolver‑level blocks.
- Risk of over‑blocking exists; appeal routes and transparency matter.
Managed service providers (MSPs)
- Offer baseline protection with low overhead by enforcing resolver policies at the edge.
- Combine with logging, alerting, and incident response for coverage beyond DNS.
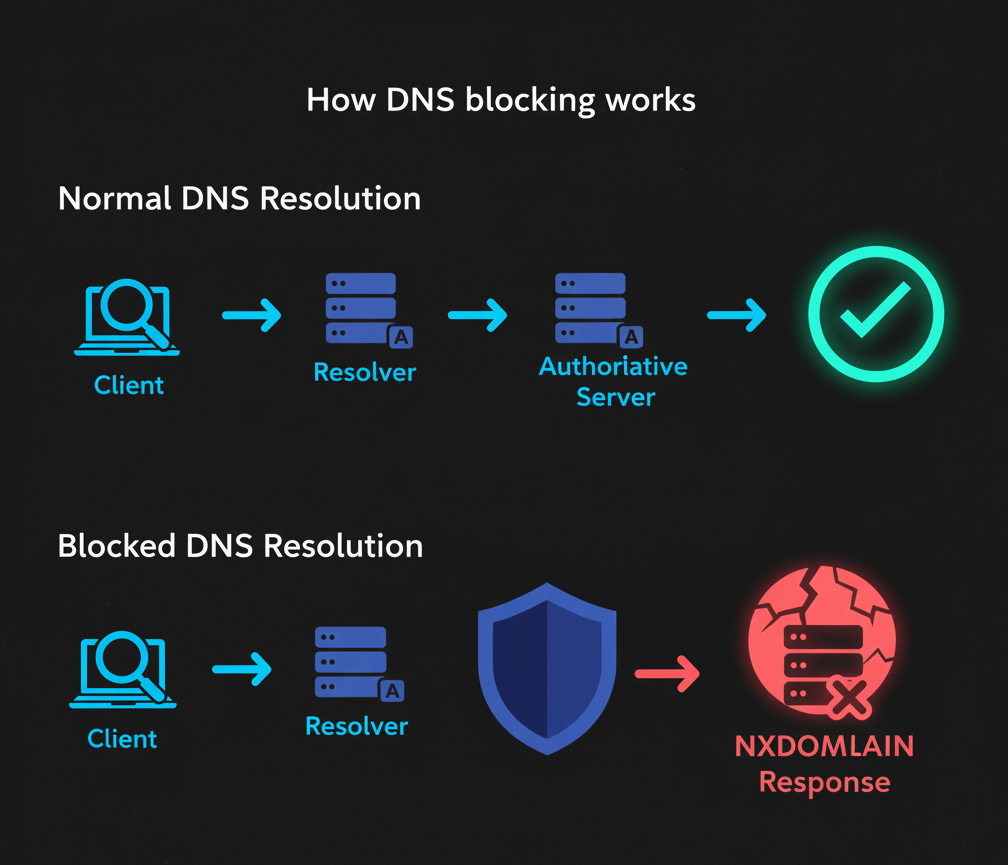
How DNS blocking works
Common techniques
- NXDOMAIN / NODATA — the resolver replies that the name does not exist or has no records.
- Sinkholing — reply with a safe IP that shows a block page or a null IP like
0.0.0.0. - RPZ — Response Policy Zones let operators apply policy feeds to modify answers.
- REFUSED — the resolver declines to answer for that name.
Where filtering happens
- On your resolver — a public DNS service or your ISP's resolver applies policy lists.
- On your network — a firewall, Pi‑hole, or enterprise gateway enforces rules.
- At the ISP — court orders or voluntary codes lead to resolver‑level blocks.
DNS RESOLUTION FLOW
Understanding how DNS resolution normally works helps explain where blocking occurs. Here's the typical flow from user request to website response:
DNS resolution process
Note
DNS blocking only affects traffic looked up by name. It does not block direct IP connections or traffic already established at other layers.
Security vs. censorship
Security resolvers block domains linked to malware, phishing, or command‑and‑control. Policy blocks restrict legal but unwanted categories, or enforce legal orders. Over‑blocking and collateral damage can occur in both cases, so good providers publish clear policies and appeal routes.
Encrypted DNS (DoH / DoT)
Encrypted DNS protects queries between your device and the resolver. DNS over HTTPS (DoH) wraps DNS in HTTPS. DNS over TLS (DoT) uses TLS on port 853. Encryption hides the query from local networks and ISPs, but it does not bypass blocking done by the resolver you choose, and it does not defeat IP‑level blocks.
Check if you use encrypted DNS
- Visit your resolver's test page (e.g., Cloudflare's /help).
- Run:
curl -I https://dns.google/dns-queryor use your resolver's DoH URL.
Trade‑offs
- Enterprises often terminate or proxy DoH/DoT to keep security visibility.
- Captive portals may fail until DoH is disabled or allowed.
Public resolvers with blocking options
Here's a quick comparison of popular DNS resolvers that offer filtering. For detailed setup guides and more options, see our Safe Resolvers page.
Cloudflare 1.1.1.1 for Families
Malware / +Adult filtering
IPv4: 1.1.1.2 / 1.1.1.3
DoH: security.cloudflare-dns.com/dns-query (malware)
family.cloudflare-dns.com/dns-query (malware+adult)
Choose malware‑only (.2) or malware+adult (.3)
Privacy Policy • 24h retention
Quad9
Security only
IPv4: 9.9.9.9
Blocks malicious domains; no content categories
Privacy Policy • No retention
OpenDNS FamilyShield
Pre‑set family filters
IPv4: 208.67.222.123 / .220.123
Fixed policy; for custom rules use OpenDNS Home/Umbrella
Privacy Policy • 7 days retention
CleanBrowsing
Family / Adult / Security
IPv4: 185.228.168.168 (Family)
Multiple free presets; paid custom policies
Privacy Policy • 24h retention
AdGuard DNS
Ads/Trackers / Family
IPv4: 94.140.14.14 (Default)
Ad/tracker blocking with optional family filter
Privacy Policy • 24h retention
NextDNS
Custom policies
Provider URL per account
Highly configurable (account required)
Privacy Policy • Configurable retention
💡 Pro tip: Want more details? Check out our comprehensive resolver guide with setup instructions and security comparisons.
How to test if DNS blocks are active
Command‑line
# Replace RESOLVER with your DNS, e.g. 9.9.9.9
# Query a known test domain from your provider
# Example: Quad9 test (returns blocked)
dig @RESOLVER test.quad9.net TXT +short
# Test DoH endpoint directly (JSON format example)
curl "https://cloudflare-dns.com/dns-query?name=example.com&type=A" \
-H "accept: application/dns-json"
Browser checks
- Visit Cloudflare's connection check.
- Open provider "welcome" or "status" pages to confirm you are using their resolvers.
Bypass and limitations
🔐 Encrypted DNS
Can bypass ISP‑level DNS blocks if you choose an external resolver, but the chosen resolver's own policies still apply.
🌐 VPNs
Replace your transport path and DNS, so local DNS blocks usually no longer apply. Network or legal blocks placed on the destination IP will still bite.
📍 Direct IP access
Avoids name‑based blocking but many sites serve nothing useful on bare IP or check SNI/Host headers.
False positives and transparency
If a domain is wrongly blocked
- Confirm exact hostname and record type; retest via a second resolver.
- Collect evidence (whois, hosting, malware scans) and file an appeal.
- Use a temporary allow-list; document the exemption.
What good providers publish
- Category definitions, data sources, and retention/IP handling.
- Change history and SLA for fixes; an appeal route.
DNS security best practices
Redundancy and availability
- Run at least two resolvers and two authoritative servers where applicable.
- Use anycast or geographically separated instances to avoid single points of failure.
Access control and exposure
- Restrict resolver access to your networks; prefer authenticated channels for admin.
- Hide management interfaces from the public internet; apply least privilege.
Logging and monitoring
- Enable resolver logs with retention that matches your policy and privacy promises.
- Alert on spikes in NXDOMAIN, SERVFAIL, or unusual query volumes; investigate cache poisoning signals.
Cache hygiene
- Use cache locking to prevent premature overwrites before TTL expiry.
- Flush selectively during incidents to avoid unnecessary outages.
DNSSEC validation
- Turn on DNSSEC validation on your resolvers to detect tampering in signed zones.
- Monitor for validation failures and have a temporary bypass procedure.
Change control
- Version and test blocklists/RPZ feeds before rollout; document exemptions and appeals.
- Review categories periodically with stakeholders to reduce over‑blocking.
Glossary
- Resolver
- Server that answers DNS queries on your behalf, usually recursively.
- RPZ
- Response Policy Zone. A policy feed that lets resolvers modify answers (e.g., blocking).
- NXDOMAIN
- \"Non‑existent domain\" response.
- Sinkhole
- Return of a safe IP (or 0.0.0.0) to divert traffic.
- DoH / DoT
- Encrypted DNS transport over HTTPS or over TLS.
FAQ
Does encrypted DNS bypass ISP DNS blocks?
Yes, if the block is only at your ISP's resolver and you switch to an external encrypted resolver. It will not bypass blocks enforced by your chosen resolver or blocks at IP/HTTP levels.
Can DNS blocks stop all harmful sites?
No. DNS filters reduce exposure but can be bypassed and cannot see inside encrypted web traffic. Use layered controls.
Is DNS blocking legal where I live?
It depends on jurisdiction and purpose. Follow local law and organisational policy.